Dave Tingling's public portal
Say hello...we're excited to connect! 🔒
“Boy I've got vision and the rest of the world wears bifocals ” ---Butch Cassidy chacter in ``Butch Cassidy and the Sundance Kid''
Say hello...we're excited to connect! 🔒
“Boy I've got vision and the rest of the world wears bifocals ” ---Butch Cassidy chacter in ``Butch Cassidy and the Sundance Kid''
Welcome ▸ Publishing lab results ▸ Scheemsly
Yup, scheemsly. My closest friends and I pronounce it like you would the English word "scheme," turned into an adjective. There's more to that story, but let's just say it's our little term for advanced, special and secret projects. We have a definition, etymology, and correctly diacriticized version somewhere. For now just consider all that secret ;-).
The attached (or linked) visualization correlates the TCP model of internetworked systems, and proposes a distinction between “infrastructure” and “applications”, purely for practical working reasons.
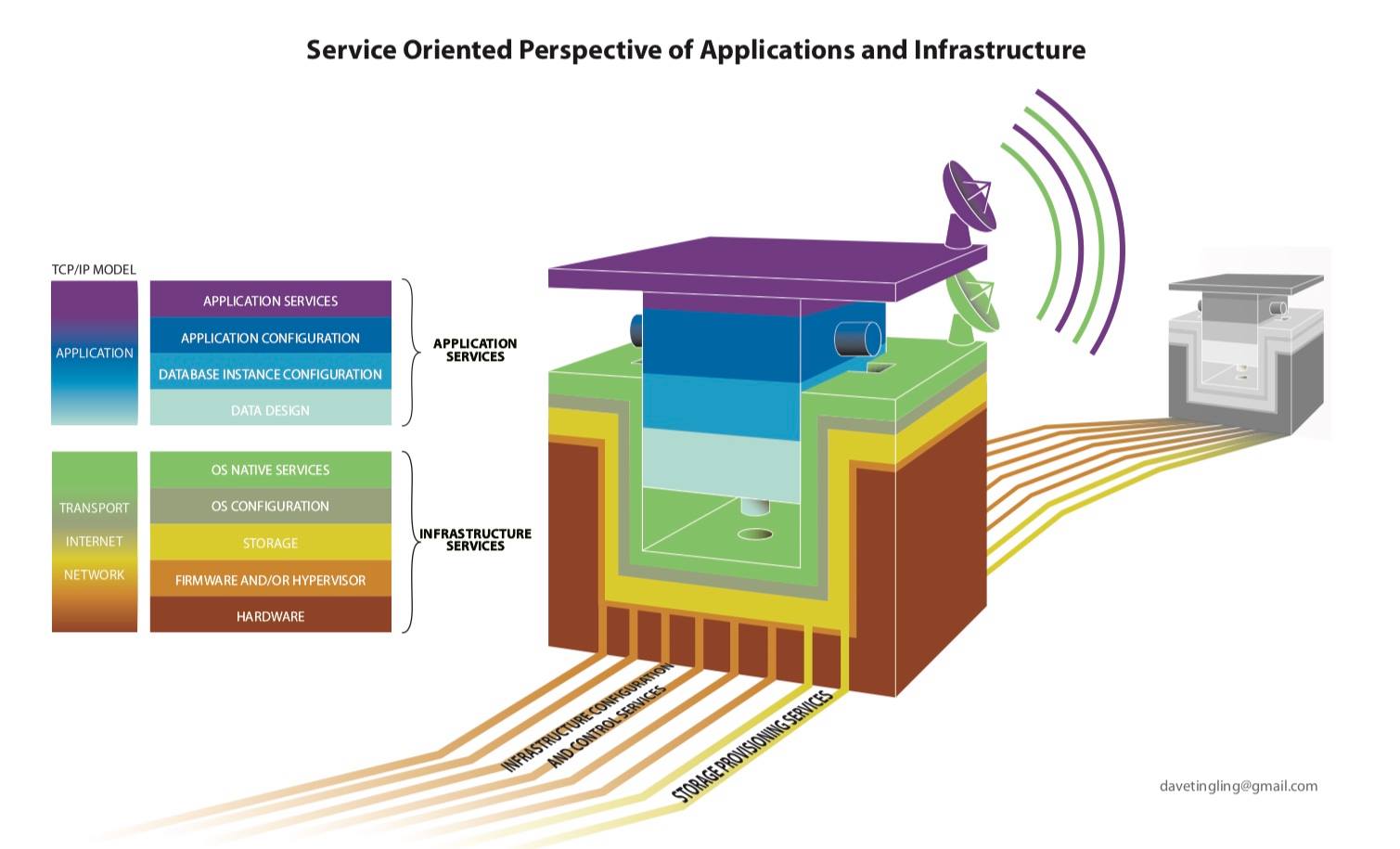
Please contact me to let me know if you found some value in this diagram.
I’ll have to do some research and have a word with Sir Tim Berners-Lee on this one. I don’t believe it has been done yet. But the title has given it away, too :-)
The problem of “burgeoning complexity” has rendered the Internet almost useless as a tool to rapidly identify accurate and correct information. Distinguishing published “signal” from “noise” is a challenge that massive collaborative technology itself has not met.
Google, Wikipedia and other notable efforts exist to sort and aggregate the “noise.” Various innovations have approached ‘truth’ problems from important angles, but at best address only one or two critical failings (or logical fallacies) of previous efforts.
This work outlines a mathematical and technical methodology “Towards an Effective Global Information Management System.” I present ideas crossing disciplinary field boundaries; although no rigorous mathematics are presented, I assume the reader has a strong computer science, engineering, and/or mathematics background, and “architecturally” understands first principles of:
* Cryptography,
* Game theory,
* Distributed computing,
* Linguistics,
* Logic,
* Neural networking,
* Statistical analysis,
* Very Large Scale Intergation (VLSI), and
* Queuing theory.
In the course of researching this work, we applied biomimetics by simulating dual-processor systems programmed to function according to theoretical models of the human brain.
Investors are invited to learn more. For more information, please contact me using my first name (Dave) [at] streamlines [dot] biz.
Traditional plain old telephone systems (POTS) worked with a simple binary result. From a design perspective, a call was either made (the line rings) or the line was busy.
Later, voicemail extended that model by introducing something than can be considered as an intermediate system state, depending on the duration of the ring. Functionally, the original communication is intercepted, the message queued for later delivery.
Today, smartphones, network provider capacity, and IP telephony allow complex communication system scenarios among hardware vendors, application developers, and telcos.
We propose that a given caller, in the event of a “busy” or “service unavailable” condition, should be able to receive a CUSTOMIZED message, pre-recorded by the subscriber and matched to the identity of the inbound caller. Several architectural executions of this function are possible.
In practice, let’s say you knew your phone’s battery was about to die, or let’s say you knew beforehand that you’d be in a lobby where no cellular calls are permitted. Or perhaps you are going to be driving and don’t want to be distracted by any conversation. Nonetheless, you are expecting important calls.
Our proposed system would recognize the inbound caller (by caller ID), and deliver a unique message (which you have pre-designated only for that caller and/or that time of day). Three different callers might try to reach you (at around the same time) while you (not your machine) are in this state, and our system processes them, as follows:
Your calling family member might hear: “Honey, I’m tied up but I’ll be there in 15 minutes!”
Your calling boss might hear a more professional: “I’m not available right now, but I’ll definitely get the report off before the end of the day!”
You client might hear: “I’m not at my desk right now, but please leave me a message.”
Our system can define groups of inbound callers for a single message. It may ensure that certain specific callers always receive your unique denial of service message (irrespective of the device/or network’s availability). Further, these and other features may be configured, then enabled or disabled at will by the subscriber, using the handset only.
The end result is a dynamic network that is personally tailored—adapting to and serving the desired state of the human endpoint (as opposed to simply the handset’s state).
Mobile subscribers today are still forced to work within service constraints that evolved from the POTS. Unfortunately, they have come to believe that “accept call” or “reject call” are the only decisions they can make to govern their service and describe their availability status—“Let it go to voicemail” or not. Given today’s technologies, that model is outmoded and mediocre, at best. Our proposed adaptive messaging platform empowers creative communication patterns among subscribers, and may even encourage future generations to re-discover the value of human interaction via the spoken word.
Questions? Call Dave at 352-505-7885.